Phishing, Spear Phishing & Spoofing
Phishing is email attempting to trick people into giving out their passwords or other personal information. It is generally sent to a wide group of people, literally "fishing" for information. Phishing will often include links to websites meant to look like other websites. Often they will try to mimic email, help desk, or other IT support pages.
Spear phishing is email attempting to trick a specific person into providing their passwords or often financial information. Spear phishing will usually look like it comes from a superior or coworker, and will often create a sense of familiarity (multiple emails in the exchange before the ask) or urgency to pressure the user into complying.
Always look at the sending email. Is it a gmail, hotmail or yahoo address? Ignore it. Remember, the names and positions of University staff can be easily found on the internet!
Spoofing is any email that looks like it comes from someone other than the actual sender. A threat actor may send an email spoofed as a CEO's email address.
Most spoofing is caught by our spam filters. Still, always use common sense when responding to an email asking for financial or sensitive information!
How To Protect Yourself
If you think you have received a phishing or other misleading email, please ask someone to verify it. You could call the sender, or find them in person if possible, to verify that they actually sent the email. You can save the message as an attachment, and forward it to iso-alert@som.umaryland.edu for verification.
Whatever you do, do not respond to the phishing message for any reason, including trying to scold or taunt the sender. Any response you send can give the attacker information, even if it's just that your email address is valid.
Be especially skeptical of emails with an External tag on it. These emails are not originating from SOM or elsewhere on campus.
Outlook in a browser:

Outlook desktop client:
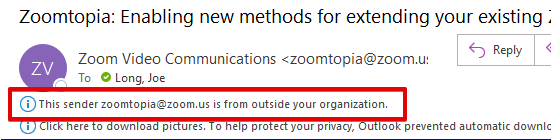
Hover over links before you click on them. Make sure the link that is displayed in the email is the same as the actual link.
Here is a link for our help desk ticketing system. When I hover my arrow over the link text, the actual link shows up. We can see here, it is the same.
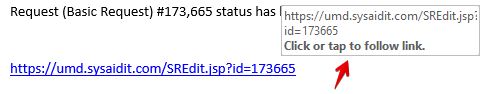
Here is another link, but when I hover over this one, I can see that they are not actually the same link at all!
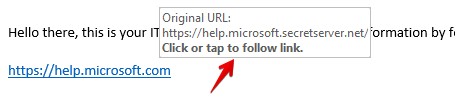
In the same way that I can write an email where the words Learn More Here become a link, I can also make a link that shows one URL and goes to another.
And always remember that what is to the right of a URL is the most important. Anything that ends in umaryland.edu is owned by UMB/CITS. Anything that ends in som.umaryland.edu is owned by SOM. You can safely assume a URL such as password.som.umaryland.edu is legitimate, but a URL like som.umaryland.password.com would not be.
